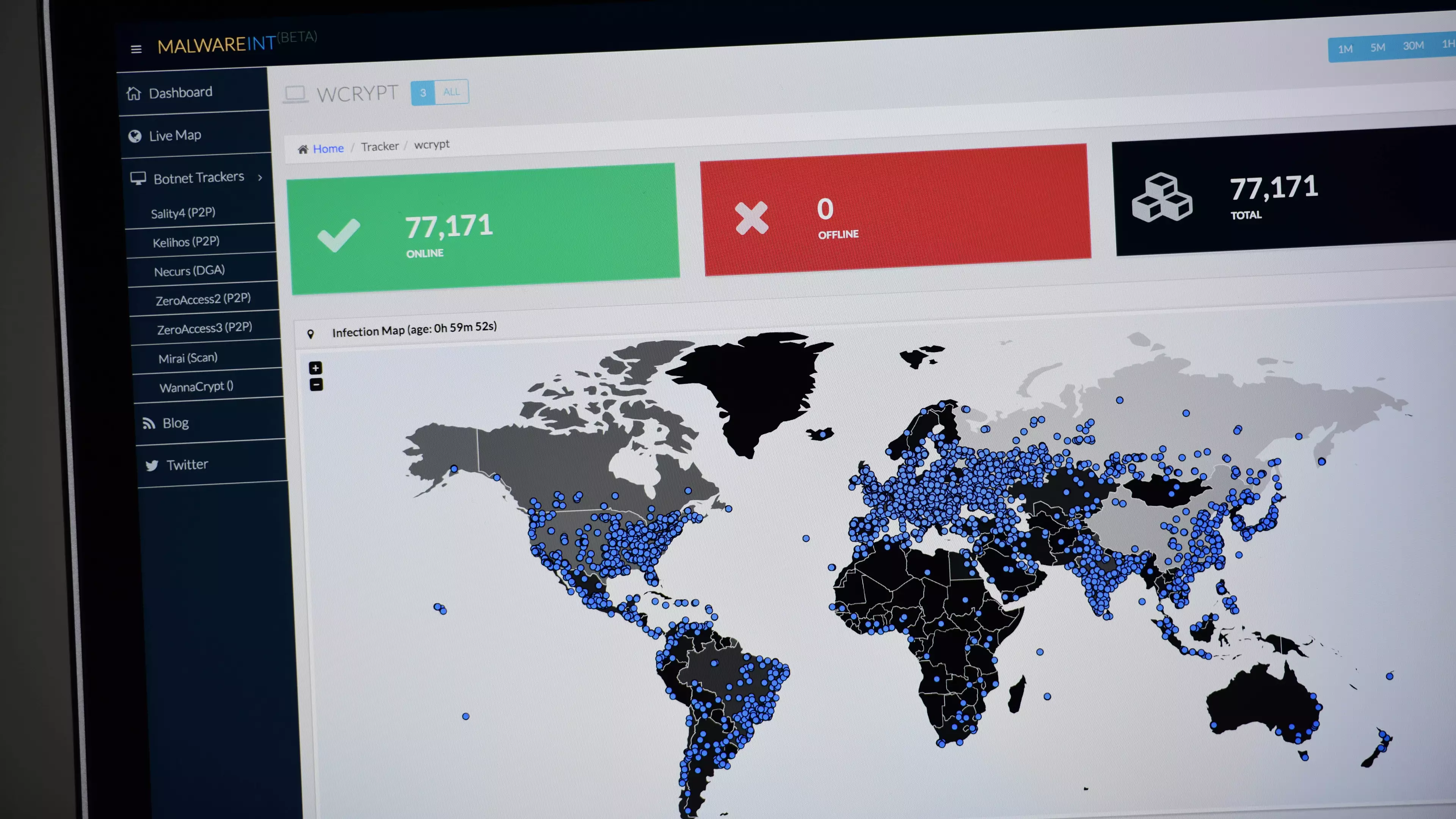
There was panic across some NHS hospitals yesterday after a cyber-criminal launched an attack by using ransomware. As a result, x-rays and operations had to be postponed as doctors couldn't access certain information.
The malware was designed to encrypt data on a user's computer and then it demands a sum of money in exchange for unlocking the device.
Advert
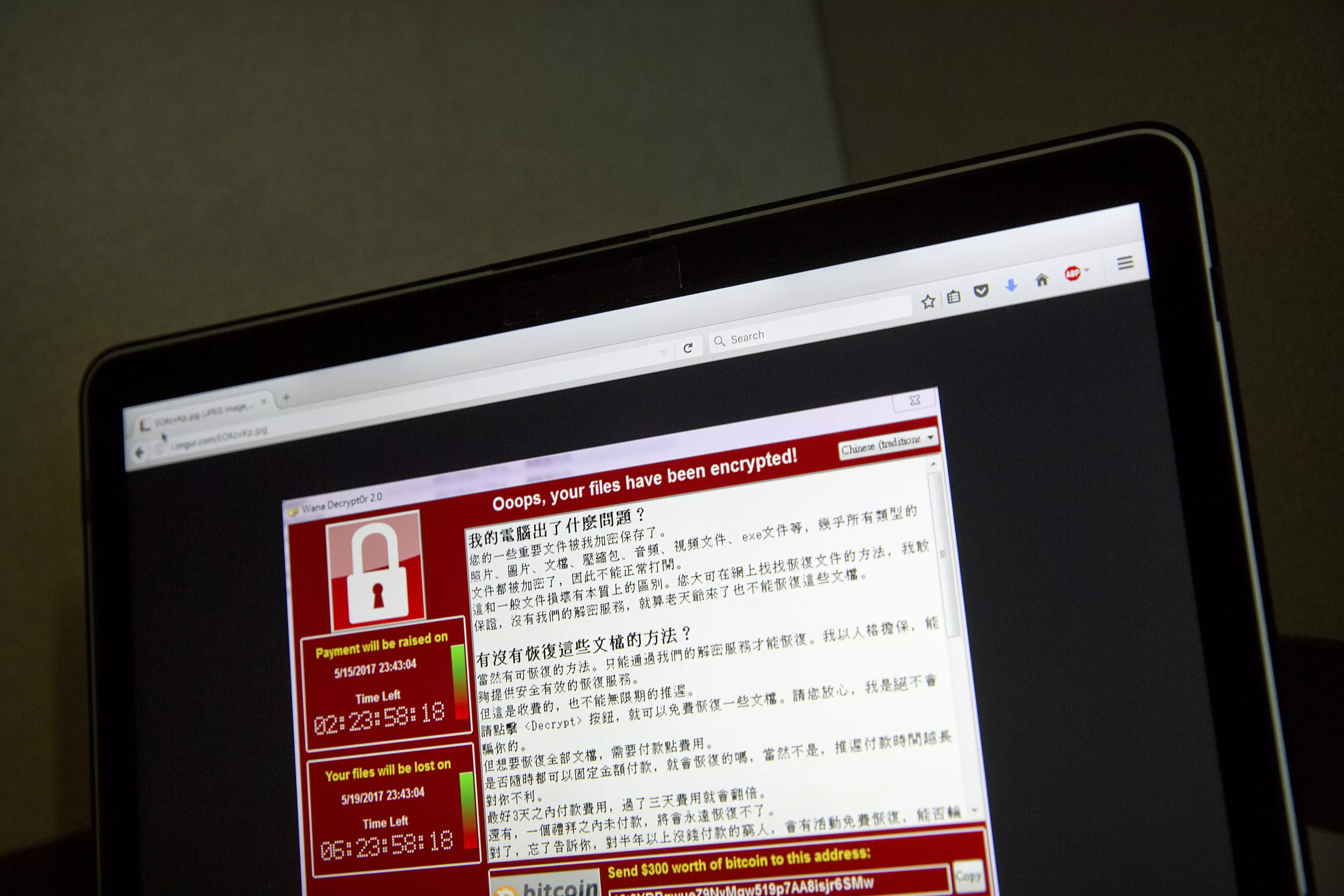
The message in the ransomware says: "Many of your documents, photos, videos, databases and other files are no longer accessible because they have been encrypted. Maybe you are busy looking for a way to recover your files, but do not waste your time. Nobody can recover your files without our decryption service.
"You only have three days to submit the payment. After that the price will be doubled. Also, if you don't pay in seven days, you won't be able to recover your files forever."
Credit: PA
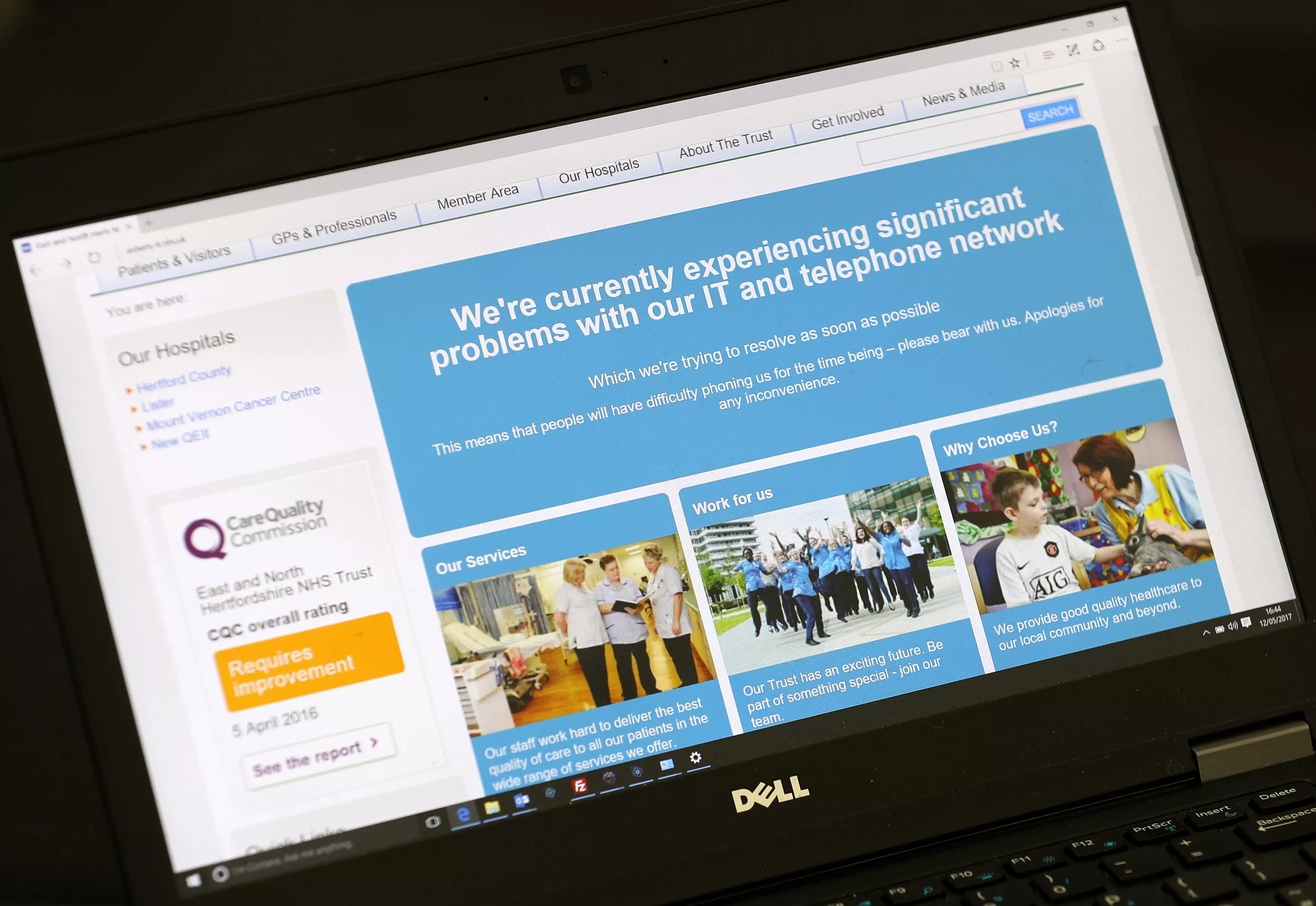
But the NHS wasn't the only target. The attack hit nearly 100 countries and affected tens of thousands of computers at major companies like FedEx and Telefonica. But a UK cyber security expert has explained just how he managed to tackle one of the biggest ransomware attacks in history.
Twitter user @MalwareTechBlog says on his blog: "Although ransomware on a public-sector system isn't even newsworthy, systems being hit simultaneously across the country. I was quickly able to get a sample of the malware with the help of Kafeine, a good friend and fellow researcher. Upon running the sample in my analysis environment, I instantly noticed it queried an unregistered domain, which I promptly registered."
He's also uploaded a video of how the ransomware spread across countries:
MalwareTechBlog adds: "Now you probably can't picture a grown man jumping around with the excitement of having just been ransomwared, but this was me.
Advert
"The failure of the ransomware to run the first time and then the subsequent success on the second mean that we had in fact prevented the spread of the ransomware and prevented it ransoming any new computer since the registration of the domain."
According to The Guardian, he purchased the domain name for a little more than $10 (£7.76). While it didn't help Europe or Asia, which was struggling to cope with the outbreak, it gave America enough time to build up its defences.
Credit: PA
Advert
UK Home Secretary, Amber Rudd, hasn't confirmed whether NHS computers have been backed up, but they will have their software upgraded to prevent an attack like this in the future.
The attack was eerily launched a day after Dr Krishna Chinthapalli's article in the British Medical Journal was published, warning about this exact type of attack.
Featured Image Credit: PA